In the previous post we explained how to setup a SSH connection between a Monero wallet and a Monero node. In this post we will explain how to create a similar setup with a Tor onion service. The setup works with the graphical user interface (GUI) and the command line interface (CLI). And should work with Linux, FreeBSD and OpenBSD.
Why use a Tor onion service to connect to a remote Monero node
Some features:
- End-to-end encryption by default
- Does not require you to open ports on a NAT router or firewall
- Can work around censorship on the client and server side
- Can hide the ip address of the Monero node and the Monero wallet client
In short it can increase the privacy and security between a wallet and a node. The setup can be useful when SSH is not an option or not providing enough privacy.
How to setup a Tor onion service
The instructions are for Debian and Ubuntu based systems. But the general principles are the same across other systems.
Use the following instructions on the Monero blockchain node:
- Checkout the official Tor installation instructions to install latest version of Tor. Follow the steps in “Option two: Tor on Ubuntu or Debian“.
- Open the Tor configuration file:
- Look for the line starting with “#HiddenServicePort 80 127.0.0.1:80” and add these lines below it to configure the Tor onion service:
- Reload Tor configuration:
- Get the Tor .onion hostname:
- Start the blockchain synchronization service on the Monero node. You don’t have to give it any special configuration options:
- The Monero daemon should now be available via the Tor onion service.
sudo nano /etc/tor/torrc
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 18081 127.0.0.1:18081
sudo service tor restart
sudo less /var/lib/tor/hidden_service/hostname
This will output the Tor onion service hostname, for example: “n77nqhcj7znz4h6p.onion“. You use this hostname on the Monero wallet system to connect to the Monero node.
./monerod
Or when you want to run the daemon in the background:
./monerod --detach
Public vs private Tor onion service
By default the Tor onion service names are published on the Tor network. And everyone who knows the hostname is able to connect to your Monero node. If you want to keep your service private you can protect it with an authentication key or “auth cookie“. Use the following steps to protect the onion service with an authentication key:
- On the Monero node you open the Tor configuration file:
- Add clients to the configuration with the “HiddenServiceAuthorizeClient …” option (you can change “moneroclient1” to another name):
- Restart Tor:
- View the authorization keys for the clients:
- On the Monero wallet system you need to configure the hostname and the authorization key in the Tor configuration. You do this with the “HidServAuth” option. This will be explained in the section below.
sudo nano /etc/tor/torrc
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 18081 127.0.0.1:18081
HiddenServiceAuthorizeClient stealth moneroclient1
It is possible to provide up to 16 different clients with the stealth option. Just add a comma between the client names. Example:
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 18081 127.0.0.1:18081
HiddenServiceAuthorizeClient stealth moneroclient1,moneroclient2,moneroclient3
sudo service tor restart
sudo less /var/lib/tor/hidden_service/hostname
Example output with 3 clients:
n77nqhcj7znz4h6p.onion lm+Byxo+i6gYBMj+OFba2R # client: moneroclient1
vj4bt5wx77gaauxw.onion TyU3BNZ1Px6c/o0xQUfqcx # client: moneroclient2
clsaxznmhy7lpxqr.onion SKwtlxjAUPHD1tdYrsQ7UR # client: moneroclient3
The first column is the hostname, the second column is the authorization key and the last column is the client name.
For example:
The client named “moneroclient1“, will use the hostname “n77nqhcj7znz4h6p.onion” with authorization key “lm+Byxo+i6gYBMj+OFba2R“.
Connect the Monero wallet to the Monero onion service
Use the following steps on the Monero wallet system:
- Checkout the official Tor installation instructions to install latest version of Tor. Follow the steps in “Option two: Tor on Ubuntu or Debian“.
- Optional: If you run a private onion service you need to add the Tor hostname and authorization key to the Tor configuration:
- Start the Monero wallet with the following command (change “tor-hostname” to the correct .onion hostname):
- Monero wallet GUI command:
- It might take a couple of seconds before the Monero wallet is connected to the Monero daemon.
- After your wallet is synced to the latest blockchain updates you can use it to check the current balance and send transactions.
sudo nano /etc/tor/torrc
Add the following line at the beginning of the file (change “onion-address” and “authorization-key” to the correct values):
HidServAuth onion-address authorization-key
Example with “moneroclient1“:
HidServAuth n77nqhcj7znz4h6p.onion lm+Byxo+i6gYBMj+OFba2R
Restart Tor to load the changes:
sudo service tor restart
torsocks ./monero-wallet-cli --daemon-host tor-hostname.onion
Example:
torsocks ./monero-wallet-cli --daemon-host n77nqhcj7znz4h6p.onion
torsocks ./monero-wallet-gui
If you open the GUI for the first time you need to set the daemon address from ‘localhost‘ to the .onion hostname. On the first screen you select your preferred language. The second screen allows you to set the ‘Custom daemon address‘. You need to add the full .onion address. Example: n77nqhcj7znz4h6p.onion:18081
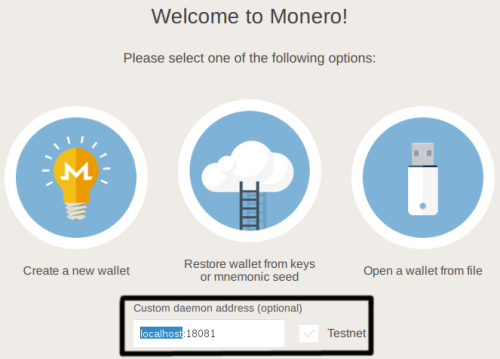
Change localhost to the .onion hostname:
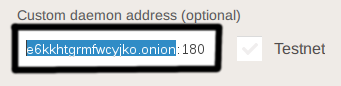
Verify that the .onion hostname is set:
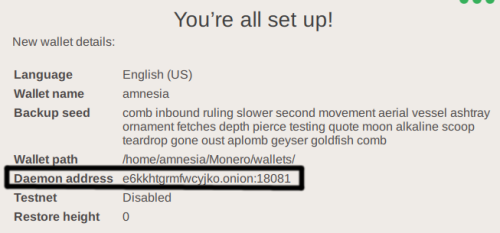
You can also change the address via the ‘Settings‘ tab. Configure the .onion address in ‘Daemon address‘ and click on ‘Connect‘ to start the connection to the .onion daemon.

List of public Monero .onion nodes
Right now we are only aware of one public .onion Monero node. That is the one from sigaint, a privacy oriented email provider. If you have a .onion Monero node and would like to share it with others, you can leave a comment below with your .onion hostname. Feel free to add your Monero address and contact information. We request you to play nice with people who use your service and don’t collect information of them.
Note: Using a Monero node from a third party has privacy implications. Use them at your own risk. We recommend to use your own node whenever possible.
List of public Tor .onion Monero nodes:
anvt4eu43a2svno3.onion
o6nvntbo3qsn36dm.onion
Don’t forget to leave a comment when a .onion address is no longer working.
The next article will explain how to combine SSH forwarding with a Tor onion service. SSH will provide an extra layer of encryption and will provide more flexible authentication methods. This can be a valuable option for high security environments.
Support
If you have any questions, comments or suggestions you can leave a comment below or send an (encrypted) email.
You can support us by donating to:
Bitcoin:
1Ndk6vc9PST9aCHiyd8R2PAXZ68HxeKSgn
Monero:
463DQj1ebHSWrsyuFTfHSTDaACx3WZtmMFMwb6QEX7asGyUBaRe2fHbhMchpZnaQ6XKXcHZLq8Vt1BRSLpbqdr283QinCRK


6 thoughts on “Monero: How to connect a wallet to a Tor onion service node”